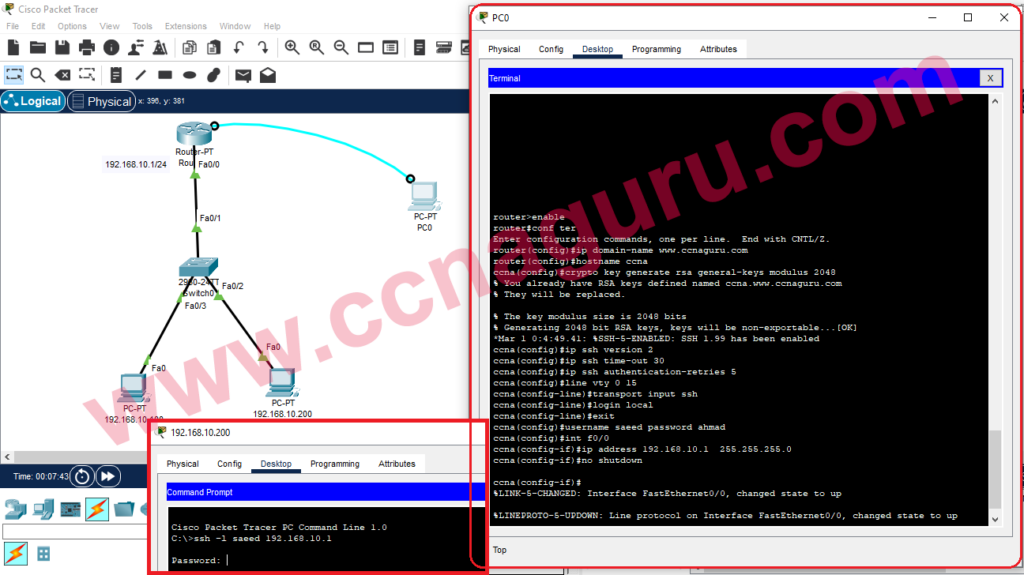
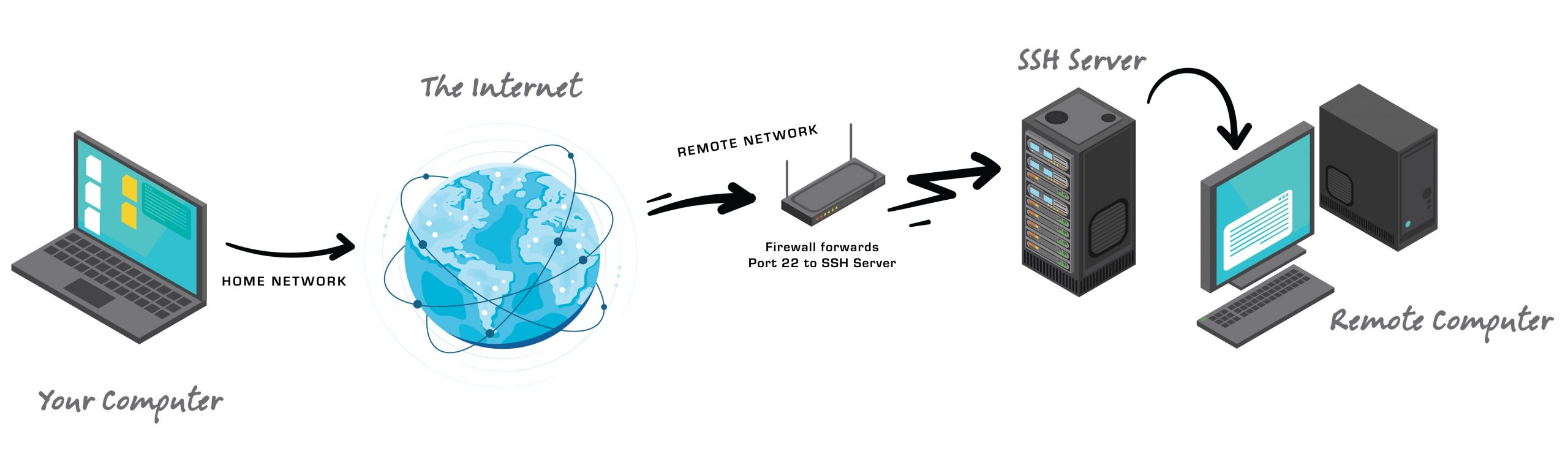
In today's digital landscape, securing remote SSH access is more critical than ever before. As more businesses and individuals rely on remote work, ensuring the security of your SSH connections is paramount to protect sensitive data and maintain operational integrity.
SSH (Secure Shell) is a cryptographic protocol that provides secure access to remote servers. It serves as a vital tool for system administrators and developers who need to manage servers remotely. However, with its widespread use comes the risk of unauthorized access and cyberattacks. This guide aims to provide you with actionable strategies to secure your SSH connections effectively.
Whether you're a beginner or an experienced IT professional, understanding how to safeguard your SSH access is essential. By implementing the techniques outlined in this article, you can significantly reduce the risk of security breaches and protect your infrastructure from malicious actors.
Read also:Hdhub4u Com In Bollywood Movies Your Ultimate Guide
Table of Contents
- Introduction to SSH and Its Importance
- Basic Principles of Securing Remote SSH Access
- Enhancing SSH Authentication Methods
- Configuring SSH for Maximum Security
- Implementing Firewall Settings for SSH
- Monitoring SSH Connections for Suspicious Activity
- Long-Tail Keywords: Advanced SSH Security Techniques
- Best Practices for Securing Remote SSH Access
- Common SSH Attacks and How to Prevent Them
- Future Trends in SSH Security
Introduction to SSH and Its Importance
SSH, or Secure Shell, is a network protocol that facilitates secure communication between a client and a server over an unsecured network. It is widely used for remote server management, file transfers, and tunneling. The importance of SSH lies in its ability to encrypt data, ensuring that sensitive information remains protected from unauthorized access.
With the rise of remote work and cloud computing, the demand for secure SSH access has surged. Businesses rely on SSH to manage critical infrastructure and applications, making it a prime target for cybercriminals. As such, securing remote SSH access is not just a recommendation but a necessity for maintaining cybersecurity.
In this section, we will explore the fundamental aspects of SSH and why securing it is crucial for your organization's security posture.
Basic Principles of Securing Remote SSH Access
Understanding SSH Vulnerabilities
Before diving into the methods of securing SSH, it is essential to understand the vulnerabilities that can be exploited. Weak passwords, outdated software, and misconfigured settings are common entry points for attackers. By addressing these vulnerabilities, you can significantly enhance the security of your SSH connections.
Here are some basic principles to consider:
- Use strong and unique passwords for all SSH accounts.
- Disable root login to prevent direct access to the system's administrative account.
- Limit the number of login attempts to thwart brute-force attacks.
Regularly Updating SSH Software
Keeping your SSH software up to date is crucial for addressing known vulnerabilities. Software updates often include security patches that fix bugs and protect against newly discovered threats. Schedule regular updates and ensure that your systems are running the latest stable version of SSH.
Read also:Exploring The Beauty And Allure Of Emma Anthurium
Enhancing SSH Authentication Methods
Authentication is a critical component of securing remote SSH access. Traditional password-based authentication, while convenient, can be easily compromised. To enhance security, consider implementing more robust authentication methods such as public key authentication and two-factor authentication (2FA).
Public Key Authentication
Public key authentication involves generating a pair of cryptographic keys: a public key and a private key. The public key is stored on the server, while the private key is kept secure on the client's machine. This method eliminates the need for passwords and provides a higher level of security.
Two-Factor Authentication
Two-factor authentication adds an extra layer of security by requiring users to provide two forms of identification before gaining access. This can include something the user knows (password) and something the user has (a one-time code generated by an authenticator app).
Configuring SSH for Maximum Security
Proper configuration of SSH is essential for maximizing its security. The SSH configuration file, typically located at /etc/ssh/sshd_config, contains settings that control how SSH operates. Below are some key configurations to consider:
- Change the default SSH port (22) to a non-standard port to reduce automated attacks.
- Disable password authentication and rely solely on public key authentication.
- Specify which users or groups are allowed to connect via SSH.
By carefully configuring these settings, you can create a more secure SSH environment that minimizes the risk of unauthorized access.
Implementing Firewall Settings for SSH
A firewall acts as a barrier between your SSH server and potential threats from the internet. Configuring your firewall to allow only necessary SSH traffic can significantly enhance security. Use tools like iptables or ufw to define rules that restrict SSH access to specific IP addresses or ranges.
Limiting SSH Access by IP Address
By limiting SSH access to trusted IP addresses, you can reduce the risk of unauthorized access. This approach is particularly useful for organizations with a fixed set of remote users. However, it may not be practical for users who connect from dynamic IP addresses.
Monitoring SSH Connections for Suspicious Activity
Monitoring SSH connections is crucial for detecting and responding to suspicious activity. Tools like fail2ban and auditd can help identify and block malicious login attempts. Regularly reviewing server logs can also provide valuable insights into potential security threats.
Using fail2ban to Prevent Brute-Force Attacks
Fail2ban is a popular tool that monitors log files for repeated failed login attempts and automatically blocks the offending IP addresses. By integrating fail2ban with your SSH server, you can effectively mitigate the risk of brute-force attacks.
Long-Tail Keywords: Advanced SSH Security Techniques
In addition to the basic principles and configurations discussed earlier, there are several advanced techniques you can employ to further secure your SSH access. These techniques often involve long-tail keywords that address specific security challenges. Below are some examples:
- Implementing chroot jails to restrict SSH users to specific directories.
- Using SSH certificates for centralized authentication management.
- Enabling TCP wrappers to control access based on hostnames or IP addresses.
By incorporating these advanced techniques, you can create a more robust SSH security framework that addresses a wide range of potential threats.
Best Practices for Securing Remote SSH Access
Adhering to best practices is essential for maintaining the security of your SSH connections. Below are some key best practices to consider:
- Regularly audit your SSH configurations and server logs for potential vulnerabilities.
- Train your employees on SSH security best practices to prevent accidental breaches.
- Implement network segmentation to isolate SSH servers from other parts of your infrastructure.
By following these best practices, you can ensure that your SSH access remains secure and resilient against evolving cyber threats.
Common SSH Attacks and How to Prevent Them
SSH is a frequent target for various types of cyberattacks, including brute-force attacks, dictionary attacks, and man-in-the-middle attacks. Understanding these threats and how to prevent them is crucial for maintaining SSH security.
Brute-Force Attacks
Brute-force attacks involve automated systems trying different combinations of usernames and passwords until they gain access. To prevent these attacks, disable password authentication and use fail2ban to block repeated login attempts.
Man-in-the-Middle Attacks
Man-in-the-middle attacks occur when an attacker intercepts and alters communications between the client and server. To prevent these attacks, ensure that your SSH connections use strong encryption and verify server host keys before establishing a connection.
Future Trends in SSH Security
As technology continues to evolve, so do the methods used to secure SSH access. Emerging trends in SSH security include the use of quantum-resistant algorithms, machine learning for anomaly detection, and zero-trust architectures. Staying informed about these trends can help you stay ahead of potential threats and ensure the long-term security of your SSH connections.
Conclusion
Securing remote SSH access is a critical component of modern cybersecurity. By implementing the strategies and best practices outlined in this guide, you can significantly reduce the risk of unauthorized access and protect your infrastructure from malicious actors. Remember to regularly review and update your SSH configurations to address emerging threats and maintain optimal security.
We encourage you to take action by implementing these security measures and sharing this article with others who may benefit from it. For more insights into cybersecurity, explore our other articles and resources. Together, we can create a safer digital environment for everyone.